New ransomware campaign known as Petya
28 Jun 2017
New ransomware campaign known as Petya
First published at
9.30am
[Original version/updates]
A new ransomware campaign known as Petya is affecting computer networks using Microsoft Windows. It was first seen affecting systems in the Ukraine, but is quickly spreading across other computer networks in Europe.
To help prevent an attack, it’s critical to ensure that all systems in a network are patched. Petya gets into unpatched versions of Windows systems (XP through 2008 R2) by exploiting a vulnerability in Microsoft's Windows SMB server. If Petya enters a network through an unpatched system, it will be able to spread to any other trusted systems in the same network, even if they have been patched.
This vulnerability exploited by Petya is known as EternalBlue. Microsoft released a patch for EternalBlue, called MS17-010, in March this year.
The ransomware encrypts not only the file system on affected computers but also the Master Boot Record (MBR) in environments where the malware is able to do so.
EternalBlue vulnerability patch MS17-010 External Link/
Read more about EternalBlue External Link/
What to do
Prevention
Initial reports suggest Petya ransomware is spreading via a software vulnerability in Microsoft Windows operating systems.
• Make sure you've patched all systems in your network. Organisations using any Windows system between XP and 2008 R2 should ensure that mitigations are in place - particularly the MS17-010 Microsoft patch.
• Make sure you've backed up your system and have stored your files securely outside your network.
• If you’re not patched, consider turning the system off or disabling SMBv1 - this will stop some file sharing. These operating systems need to be either turned off or have SMBv1 disabled.
• Be careful when opening emails and clicking on links or attachments within them. They could be phishing emails that look like they've been sent by a person or organisation you know and trust.
• Ensure staff are aware of this campaign. Remind them to be vigilant about links and attachments contained in incoming emails.
Mitigation
If Petya enters your system, it will encrypt your files, blocking access to them and demanding you pay a ransom to get them back. This is what you’ll see if Petya is attempting to encrypt your files:
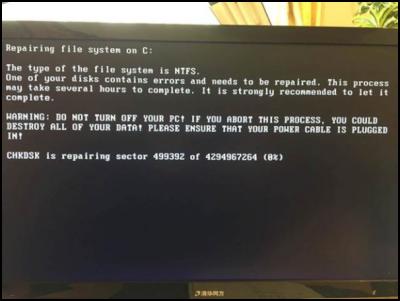
Source: Forbes.com
If you see this, turn your computer off, and don’t turn it on again. An IT specialist should be able to recover your files directly from the hard drive. If you turn your computer back on again and Petya encrypts them, there’s currently no way to retrieve them as the email address used in paying the ransom has been shut down.
More information
If you require more information or further support, submit a report on our website or contact us on 0800 CERTNZ.
Report an incident to CERT NZ


 Financial Markets Authority: FMA Seeks Clarity From High Court On Use Of Eligible Investor Certificates In Wholesale Investment Sector
Financial Markets Authority: FMA Seeks Clarity From High Court On Use Of Eligible Investor Certificates In Wholesale Investment Sector Scion: Scion’s Novel Internship Model Connects Talent With Industry
Scion: Scion’s Novel Internship Model Connects Talent With Industry Financial Markets Authority: Westpac Admits To Misleading Representations That Resulted In $6.35m In Overcharges
Financial Markets Authority: Westpac Admits To Misleading Representations That Resulted In $6.35m In Overcharges Bill Bennett: Download Weekly - Review Of 2024
Bill Bennett: Download Weekly - Review Of 2024 Bill Bennett: One NZ scores worldwide first as Starlink direct-to-mobile launches
Bill Bennett: One NZ scores worldwide first as Starlink direct-to-mobile launches Hugh Grant: How To Reduce Network Bottlenecks
Hugh Grant: How To Reduce Network Bottlenecks



