Android banking malware whitelists itself to stay connected
Symantec Security Response
Android banking malware whitelists itself to stay connected with attackers
New Android.Fakebank.B variants use social engineering to bypass battery-saving process and stay active in background
Recent variants of Android.Fakebank.B have been updated to work around the battery-saving process Doze. Variants display a pop-up message asking the user to add the threat to the battery optimisations exceptions whitelist. If this technique works, the malware stays connected to command and control servers even when the device is dormant.
Bypassing Doze
Doze is a power-saving feature in Android 6.0 Marshmallow. When a user doesn’t use an unplugged device for a period of time, the device enters Doze mode. This allows the OS to conserve battery by restricting apps' access to network and CPU-intensive services. This feature is a hurdle for banking malware running in the background and connecting to an attacker’s server to receive commands.
How the whitelisting technique works
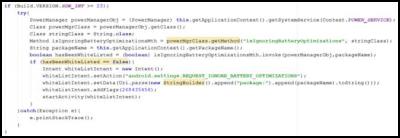
Click for big version.
Figure 1 Code responsible for triggering Battery Optimisations exceptions whitelist pop-up
The permission required to fire this intent is REQUEST_IGNORE_BATTERY_OPTIMISATIONS which is classified as normal. Marshmallow’s dynamic permission model defines permissions as either normal, dangerous, and above dangerous. Permissions determined as normal are approved automatically and cannot be disabled through appinfo permissions.
The intent causes a pop-up message to appear, as shown in Figure 2. Users may be tricked into allowing the threat to bypass Doze’s restrictions if the malware poses as a legitimate app.
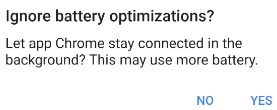
Figure 2 Malware prompt
claims that the app is called “Chrome” and requests
whitelisting
Mitigation
Symantec recommends users follow these best practices to stay protected from mobile threats:
• Keep your software up to date
• Do not download apps from unfamiliar sites
• Only install apps from trusted sources
• Pay close attention to the permissions requested by apps
• Install a suitable mobile security app, such as Norton, to protect your device and data
• Make frequent backups of important data
Protection
Symantec and Norton products detect the threat discussed in this blog as Android.Fakebank.B.
For more
information visit the Symantec Security Response blog post
available here.


 Hugh Grant: How To Build Confidence In The Data You Collect
Hugh Grant: How To Build Confidence In The Data You Collect Tourism Industry Aotearoa: TRENZ 2026 Set To Rediscover Auckland As It Farewells Rotorua - The Birthplace Of Tourism
Tourism Industry Aotearoa: TRENZ 2026 Set To Rediscover Auckland As It Farewells Rotorua - The Birthplace Of Tourism NIWA: Students Representing New Zealand At The ‘Olympics Of Science Fairs’ Forging Pathway For International Recognition
NIWA: Students Representing New Zealand At The ‘Olympics Of Science Fairs’ Forging Pathway For International Recognition Coalition to End Big Dairy: Activists Protest NZ National Dairy Industry Awards Again
Coalition to End Big Dairy: Activists Protest NZ National Dairy Industry Awards Again Infoblox: Dancing With Scammers - The Telegram Tango Investigation
Infoblox: Dancing With Scammers - The Telegram Tango Investigation Consumer NZ: This Mother’s Day, Give The Gift Of Scam Protection And Digital Confidence
Consumer NZ: This Mother’s Day, Give The Gift Of Scam Protection And Digital Confidence