Hacking Your Vote
Hacking Your Vote
By Rob Conery, WekeRoad
Blog
Sunday, September 07 2008
If you were hired to create some software to count votes in an election, how would you do it? What considerations would you have and how would you implement them. What would be your security considerations?
Think for a moment before reading on, and we'll compare your thoughts with what's actually out there. The results may surprise you.
Disclaimer: This is my personal blog and my opinions are my own and not necessarily that of my employer.
No, This Is
Not All About Touch Screens
There has been some major upset in the last few years about
touch-screen voting systems and how easy they are to
hack - but I don't want you to focus on that, for now. The
interesting thing is when you bring up "voting software"
most people think these systems are what you're talking
about.
In this case I'm more interested in how you would implement vote-counting software - the thing used to count the votes when cards are passed through a reader and tallied. Take 10 minutes or so and specifically think about:
Voting audit trails
Counting accuracy
Security
Tampering prevention
You keep on musing while we take a break to describe the election process and how votes are counted today...
How Your Vote Is
Counted
Every county has the jurisdiction to
implement an election as it sees fit, under the guidelines
of the Federal Elections Commission (FEC). This means that
every county in the US can buy and use "certified" systems
from companies such as Diebold, ES&S, and Sequoia.
One of the biggest sellers out there (the state of Maryland paid $50 Million US for this one) is the Diebold's Accu-vote. It consists of a battery of optical readers (one for each polling place) and memory cards for storing election results. It also comes with a license for GEMS, their vote-tallying and reporting software; one license per county for use by the Supervisor of Elections.
On the day that you vote, your ballot gets put into an officious looking black box with the other ballots. At the end of the day your ballot is pushed through one of these readers, and your vote is stored on one of these memory cards:

Once all of the ballots from a polling place are collected and read, a tape is printed by the optical reader that has the results on it, including a full count of the ballots read in. The election workers from that polling place sign the ticket and off it goes to the Department of Elections.
The next step in the voting chain is that the Election Supervisor (or one their appointees) takes the memory cards from each polling place and methodically plugs them into a computer running GEMS, the vote-counting software. GEMS reads the information from the cards and once all the cards are read, a final report is printed out and the Supervisor certifies the results and the election.
Seems simple enough right? Have an idea how you might implement this system?
The Diebold System
In 2003, Bev Harris
(the then-housewife and now-founder of BlackBoxVoting.org)
wanted to know more about the election software that was
being used in her home town near Seattle, WA. She got on the
internet and ran Google search after Google search until
suddenly...
... when I found that Diebold Election Systems had been storing 40,000 of its files on an open web site, an obscure site, never revealed to public interest groups, but generally known among election industry insiders, and available to any hacker with a laptop, I looked at the files. Having a so-called security-conscious voting machine manufacturer store sensitive files on an unprotected public web site, allowing anonymous access, was bad enough, but when I saw what was in the files my hair turned gray. Really. It did.
The contents of these files amounted to a virtual handbook for vote-tampering: They contained diagrams of remote communications setups, passwords, encryption keys, source code, user manuals, testing protocols, and simulators, as well as files loaded with votes and voting machine software
Turns out that Diebold kept their CVS system up on a public FTP site, with no security. Oops.
She downloaded every file she could find, which included requirements, diagrams, code, and binary files. Of particular interest to her was GEMS - the software that tallies the votes for the county.
It's a windows application written in C++, and the data is kept in an unprotected Acces database. Well that's not entirely true - the Access database is sort of protected - the GEMS application uses a password-protected DSN, with a user name of ADMIN:
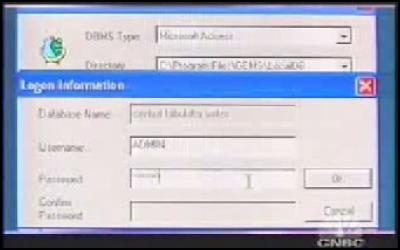
Of course if you are even a casual computer user you can just open up the Access database directly, bypassing the DSN security, and have at the results:
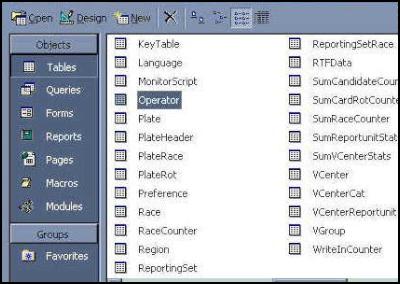
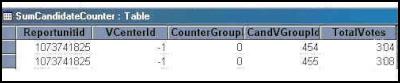
If you're wondering how easy it would be to change the results of an election (seriously) - just double-click on the SumCandidateCounter table you see there, and you can change the numbers around:
Howard Dean is shown how this works in this video:
Is this the system that you would have written? Something that gives just about anyone with motive to change an entire election result?
OK, This Was 2004. That Can't Still
Be Happening!
You might think that after all this
negative exposure, Diebold (and others) would make sure that
the system is functioning. Well you would at least hope so.
Turns out that things seem to be getting worse:
The State of California has been through the ringer with Diebold, and just this last year decertified Diebold (and many other software voting machines) completely (for the second time), and wasn't short on reasons why.
In 2006, and Diebold lost the source code again. Turns out is was stolen in Maryland - the state that paid $50 Million US for the Access database.
The State of Ohio just invested $20 Million into Diebold touch-screen systems (same ones CA banned). Turns out that a software error causes votes to be dropped. Oops. Problem can't be fixed before November 4 2008. Uh Oh. Turns out that the software doesn't like Anti-virus systems... which you'd think would be OK since a virus could comprimise the entire system. Sigh.
Our presidential election is coming up - how is your county voting? Is it using a touch-screen system? One of the ones that California has categorically thrown out, from every vendor? Or one of the buggy ones in Ohio that has a problem with Anti-virus software?
Or will your vote be stored in an Access database on an election-worker's laptop?
A More Elegant Hack
I know what you're
thinking. Buggy systems with security flaws sound like
alarmist-speak and opening up and changing an Access
database might be a bit hard; after all you'd need to be
sitting there on the computer right?
Unless the election workers aren't very protective of their hardware (from the New York Times)...
Ohio is an election battleground state with perennial problems at the polls. So what have election officials in some precincts of the state been doing to keep their voting machines safe from tampering?
Taking the machines home with them and stashing them in their garages in the days before a big election.
If it sounds like something pulled straight out of an episode of Saturday Night Live, or Borat for that matter, it’s not. The practice has become so widespread that it even has a nickname, “sleepovers.”
Meh. That's too easy and it requires some social engineering and sounds alarmist (again!). I wonder if there's a better way to hack into these machines...
Harri's Hack
In 2005 the Leon
County (Florida) Supervisor of Elections Ion Sancho
contacted BlackBoxVoting to scrutinize their
voting systems to be sure they were secure. BBV brought
along Harri Hursti, a Finnish computer
security expert. Specifically in question was the memory
card which carries the vote tallies from the local
ballot-reading (at the polling places) machines to the GEMS
counter system.
The software vendors have maintained (and still do) that there is no way to tamper with this - the card would know it has been tampered with and scramble the results. Harri, however, found differently.
Harri was given one of these cards by Ion Sancho and asked if there was any way that he could hack it. Harri took the card back to his hotel room (with a memory card reader he bought from a local computer store) and found out that the information was stored in clear text and was easily manipulated. He also found that it was possible to use negative numbers in the vote tallies, and that gave him an idea... no code needed to be written at all - the simplest of all hacks.
This is known as "Harri's Hack":
The Hursti memory card hack performed in Leon County on Dec. 13, 2005 is a variation on stuffing the ballot box prior to any votes being cast. Hursti had pre-loaded the memory card giving one candidate 5 positive votes and one candidate 5 negative votes to create a "zero report." This keeps the machine accurate in votes cast compared to number of voters.
When the scanning machines start up they make sure that the memory cards have a "zero-tally" by essentially adding the numbers together. Harri was able to get around pretty easily.
A mock election was held with the Supervisor of Elections watching, and a total of 8 votes were cast. The results were pretty clear - Harri's "stuffing" attack skewed the election results entirely, and no one had any way of knowing it. It took Harri only 30 minutes to hack the card - and the vote was completely compromised.
If you're thinking that getting access to a card or card-reader might be hard, well you can go right out and buy some from Diebold.
The Keys To The Kingdom
In 2006,
Princeton University decided to test the Diebold Accu-vote
touch-screen machine. The results are less-than
flattering:
One of the main rebuttals to this video is that, under normal situations, you can't access the hardware of a voting machine (even though they show how easy it is to pick the lock). This is true - the machines are indeed locked.
But then again you can also buy some keys from Diebold if you needed to...
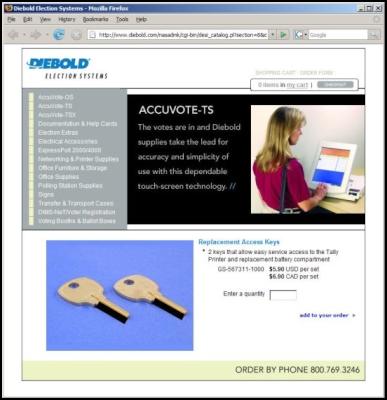
Click to enlarge
There Is So, So Much
More
As a geek I am both agitated and intrigued by
what I'm finding as I keep looking. As a voter I'm
mortified. It's important, I think, to have some
alternatives when you write a post like this so we can "keep
it positive". And here they are:
Get informed about your county and their election systems. The elections division is usually quite open and will answer most questions as it's a matter of public record. Find out what system they're using and make sure it's certified. If it's not, write a letter. You can also make a public records request of all the election results (including those signed poll tapes) if you're interested in that.
Read up on tips from BlackBoxVoting.org. They offer a great free kit for the things you can do if you're interested.
Learn more about our election process. I've only touched on the very, very tip of this issue and there are more things to be said. The documentary "Hacking Democracy" touches on a lot of these things, and you can watch it online for free. Ballots in the trash, meaningless testing results, donations to voting software companies from lobbyist groups, the State of Ohio allegedly tampering it's own election recount... It's an hour and 20 minutes - but you need to know what's going on as a voter.
Sound off! Most people are completely unaware of the election process and also the things that are being done "incorrectly". It's time that we know more about what's happening.
If you do anything at all, spend an hour and watch this HBO documentary - it's at the core of all that I've written and what motivated me to spend the last 2 weeks researching this post. I'm trying to do my part by reaching out to you as a voter - not to sling mud but to suggest that there are things you need to know more about. It's far too secret right now.
About the author:
Hi! My name is Rob Conery and I work at Microsoft. I am the Creator of SubSonic and was the Chief Architect of the Commerce Starter Kit (a free, Open Source eCommerce platform for .NET)
I live in Kauai, HI with my family, and when my clients aren't looking, I sometimes write things on my blog (giving away secrets of incalculable value).


 Gordon Campbell: On Why Leakers Are Essential To The Public Good
Gordon Campbell: On Why Leakers Are Essential To The Public Good Ramzy Baroud: Global Backlash - How The World Could Shift Israel's Gaza Strategy
Ramzy Baroud: Global Backlash - How The World Could Shift Israel's Gaza Strategy DC Harding: In The Spirit Of Natural Justice
DC Harding: In The Spirit Of Natural Justice Martin LeFevre - Meditations: Animal Encounters During Meditative States
Martin LeFevre - Meditations: Animal Encounters During Meditative States Ian Powell: Gisborne Hospital Senior Doctors Strike Highlights Important Health System Issues
Ian Powell: Gisborne Hospital Senior Doctors Strike Highlights Important Health System Issues Keith Rankin: Who, Neither Politician Nor Monarch, Executed 100,000 Civilians In A Single Night?
Keith Rankin: Who, Neither Politician Nor Monarch, Executed 100,000 Civilians In A Single Night?