Attackers after WhatsApp and Telegram users
Symantec Threat Intelligence: Attackers after WhatsApp and Telegram users
Today, Symantec has
released two new pieces of research about Android mobile
apps being exploited to attack users.
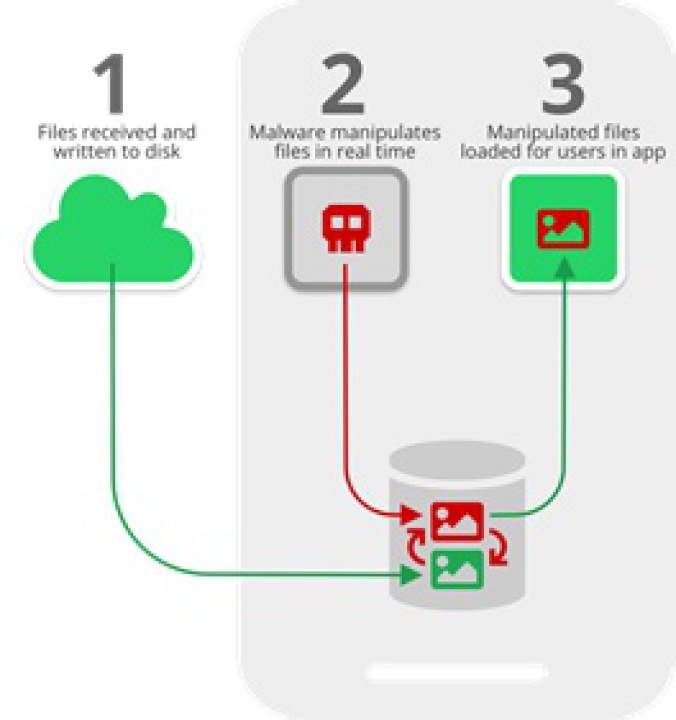
WhatsApp and Telegram media files could be exposed and manipulated by malicious actors according to new research by Symantec’s Modern OS Security team.
The security flaw, dubbed “Media File Jacking”, affects WhatsApp for Android by default, and Telegram for Android if certain features are enabled. It stems from the lapse in time between when media files received through the apps are written to the disk, and when they are loaded in the apps’ chat user interface (UI) for users to consume. This critical time lapse presents an opportunity for malicious actors to intervene and manipulate media files without the user’s knowledge.
If the security flaw is exploited, a malicious attacker could misuse and manipulate sensitive information such as personal photos and videos, corporate documents, invoices, and voice memos. Attackers could take advantage of the relations of trust between a sender and a receiver when using these IM apps for personal gain or to wreak havoc.
To read the full Threat Intelligence Report please go to https://www.symantec.com/blogs/expert-perspectives/symantec-mobile-threat-defense-attackers-can-manipulate-your-whatsapp-and-telegram-media
Additionally, Symantec has found a malicious app named MobonoGram 2019 (detected as Android.Fakeyouwon) advertising itself as an unofficial version of the Telegram messaging app and claiming to provide even more features than both the official and other unofficial versions in the market. While the app does provide basic messaging functionality, we found it was also secretly running a few services on the device without the user’s consent, as well as loading and browsing an endless stream of malicious websites in the background.
These malicious websites include Fakeyouwon, pornography and gaming websites. Symantec have also seen the URL making a request to itself, causing an infinite loop of requests to the website. Such activity not only exhausts the device’s battery, but also leads to an unpleasant user experience and may even cause the device to crash.
To read the full Report on MobonoGram 2019please go to https://www.symantec.com/blogs/threat-intelligence/unofficial-telegram-app-malicious-sites
Today, Symantec has released two new pieces of
research about Android mobile apps being exploited to attack
users.
WhatsApp and Telegram media files could be exposed and manipulated by malicious actors according to new research by Symantec’s Modern OS Security team.
The security flaw, dubbed “Media File Jacking”, affects WhatsApp for Android by default, and Telegram for Android if certain features are enabled. It stems from the lapse in time between when media files received through the apps are written to the disk, and when they are loaded in the apps’ chat user interface (UI) for users to consume. This critical time lapse presents an opportunity for malicious actors to intervene and manipulate media files without the user’s knowledge.
If the security flaw is exploited, a malicious attacker could misuse and manipulate sensitive information such as personal photos and videos, corporate documents, invoices, and voice memos. Attackers could take advantage of the relations of trust between a sender and a receiver when using these IM apps for personal gain or to wreak havoc.
To read the full Threat Intelligence Report please go to https://www.symantec.com/blogs/expert-perspectives/symantec-mobile-threat-defense-attackers-can-manipulate-your-whatsapp-and-telegram-media
Additionally, Symantec has found a malicious app named MobonoGram 2019 (detected as Android.Fakeyouwon) advertising itself as an unofficial version of the Telegram messaging app and claiming to provide even more features than both the official and other unofficial versions in the market. While the app does provide basic messaging functionality, we found it was also secretly running a few services on the device without the user’s consent, as well as loading and browsing an endless stream of malicious websites in the background.
These malicious websites include Fakeyouwon, pornography and gaming websites. Symantec have also seen the URL making a request to itself, causing an infinite loop of requests to the website. Such activity not only exhausts the device’s battery, but also leads to an unpleasant user experience and may even cause the device to crash.
To read the full Report on MobonoGram 2019please go to https://www.symantec.com/blogs/threat-intelligence/unofficial-telegram-app-malicious-sites
Today, Symantec has released two new pieces of
research about Android mobile apps being exploited to attack
users.
WhatsApp and Telegram media files could be exposed and manipulated by malicious actors according to new research by Symantec’s Modern OS Security team.
The security flaw, dubbed “Media File Jacking”, affects WhatsApp for Android by default, and Telegram for Android if certain features are enabled. It stems from the lapse in time between when media files received through the apps are written to the disk, and when they are loaded in the apps’ chat user interface (UI) for users to consume. This critical time lapse presents an opportunity for malicious actors to intervene and manipulate media files without the user’s knowledge.
If the security flaw is exploited, a malicious attacker could misuse and manipulate sensitive information such as personal photos and videos, corporate documents, invoices, and voice memos. Attackers could take advantage of the relations of trust between a sender and a receiver when using these IM apps for personal gain or to wreak havoc.
To read the full Threat Intelligence Report please go to https://www.symantec.com/blogs/expert-perspectives/symantec-mobile-threat-defense-attackers-can-manipulate-your-whatsapp-and-telegram-media
Additionally, Symantec has found a malicious app named MobonoGram 2019 (detected as Android.Fakeyouwon) advertising itself as an unofficial version of the Telegram messaging app and claiming to provide even more features than both the official and other unofficial versions in the market. While the app does provide basic messaging functionality, we found it was also secretly running a few services on the device without the user’s consent, as well as loading and browsing an endless stream of malicious websites in the background.
These malicious websites include Fakeyouwon, pornography and gaming websites. Symantec have also seen the URL making a request to itself, causing an infinite loop of requests to the website. Such activity not only exhausts the device’s battery, but also leads to an unpleasant user experience and may even cause the device to crash.
To read the full Report on MobonoGram 2019please go to https://www.symantec.com/blogs/threat-intelligence/unofficial-telegram-app-malicious-sites
ends


 Tourism Industry Aotearoa: TRENZ 2026 Set To Rediscover Auckland As It Farewells Rotorua - The Birthplace Of Tourism
Tourism Industry Aotearoa: TRENZ 2026 Set To Rediscover Auckland As It Farewells Rotorua - The Birthplace Of Tourism NIWA: Students Representing New Zealand At The ‘Olympics Of Science Fairs’ Forging Pathway For International Recognition
NIWA: Students Representing New Zealand At The ‘Olympics Of Science Fairs’ Forging Pathway For International Recognition Coalition to End Big Dairy: Activists Protest NZ National Dairy Industry Awards Again
Coalition to End Big Dairy: Activists Protest NZ National Dairy Industry Awards Again Infoblox: Dancing With Scammers - The Telegram Tango Investigation
Infoblox: Dancing With Scammers - The Telegram Tango Investigation Consumer NZ: This Mother’s Day, Give The Gift Of Scam Protection And Digital Confidence
Consumer NZ: This Mother’s Day, Give The Gift Of Scam Protection And Digital Confidence NZ Airports Association: Airlines And Airports Back Visa Simplification
NZ Airports Association: Airlines And Airports Back Visa Simplification