Espionage Group Compromises Government Agencies
Symantec Threat Intelligence – Espionage Group Compromises Government Agencies and Key Infrastructure Corporations
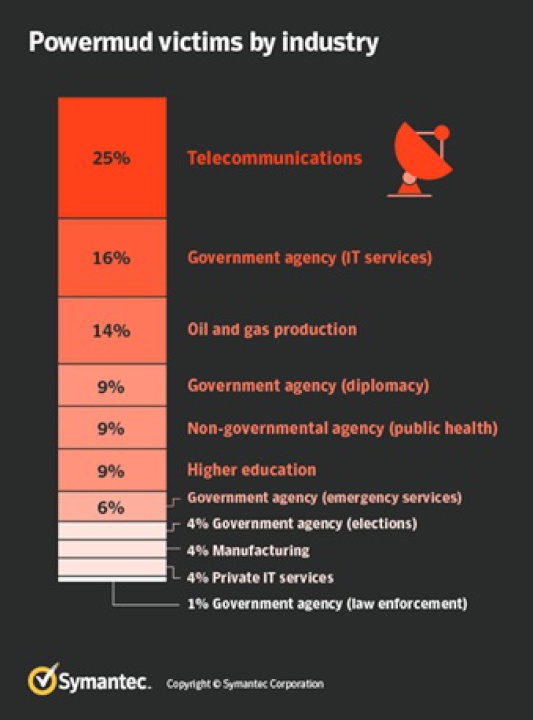
Symantec researchers have discovered the cyber espionage group, dubbed Seedworm (aka MuddyWater or Zagos), has upped its ante in recent months, infiltrating more than 30 organisations since late September. Seedworm has successfully infiltrated telecommunications firms, government agencies, NGOs, the oil & gas sector and IT services firms predominantly in the Middle East as well as multinational organisations and other companies based in Europe and the U.S.
Symantec researchers have also discovered a new Powermud backdoor, a GitHub repository used by the group to store their scripts, as well as several post-compromise tools, such as LaZagne and Crackmapexec, used to compromise victims once they have established a foothold in their network.
When Seedworm compromises a network, one of the first things it does is try to steal passwords saved in the users’ web browsers and email, demonstrating that access to the victim’s email, social media and chat accounts is one of its primary goals.
Since early 2017, Seedworm has continually updated their Powermud backdoor to avoid detection. Powermud is a custom tool used by the Seedworm group and is the only group known to use this backdoor. They’ve also gone into GitHub and used a handful of publicly available tools to carry out their work. Relying on the publicly available code is what allows it to change its operations so quickly.
To read the full Threat Intelligence Report please go to https://www.symantec.com/blogs/threat-intelligence/seedworm-espionage-group
ends


 Natural Hazards Commission: Hub Launched To Empower Architects And Engineers To Build Above Code
Natural Hazards Commission: Hub Launched To Empower Architects And Engineers To Build Above Code Harmony Energy: Ceremony Heralds Start Of Construction On New Zealand’s Largest Solar Farm Project
Harmony Energy: Ceremony Heralds Start Of Construction On New Zealand’s Largest Solar Farm Project Stats NZ: Annual Number Of Home Consents Down 7.4 Percent
Stats NZ: Annual Number Of Home Consents Down 7.4 Percent Plains Media: Plains FM Announces Name Change After 37 Years
Plains Media: Plains FM Announces Name Change After 37 Years NIWA: Flooding From Underneath - New Tool Reveals Shallow Groundwater Elevations
NIWA: Flooding From Underneath - New Tool Reveals Shallow Groundwater Elevations Commerce Commission: Commission Concludes Auckland Airport Over-charging By $190 Million
Commerce Commission: Commission Concludes Auckland Airport Over-charging By $190 Million



