Fake AV Software Updates Are Distributing Malware
Fake AV Software Updates Are Distributing Malware - Symantec Security Response
There is a new social engineering spam that attempts to trick users into running malware on their computers. Malware authors use various methods including emails pretending to be from various antivirus software companies with an important system update required to be installed by the end user, along with attaching a fake hotfix patch file for their antivirus software.
The email plays on end user concern over the lack of detection, especially in the face of the latest threats showcased in the media recently, such as the Cryptolocker Trojan. This type of social engineering entices users to open and install the hotfix without using realising what they are installing.
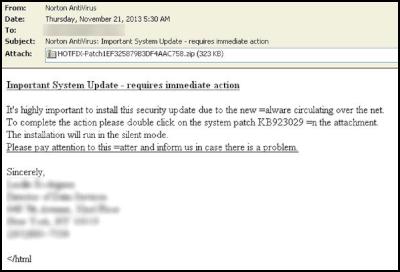
Symantec has observed a number of
different email subject lines that include many well-known
antivirus software companies (see image):
• AntiVir
Desktop: Important System Update - requires immediate action
• Avast Antivirus: Important System Update - requires
immediate action
• AVG Anti-Virus Free Edition:
Important System Update - requires immediate action
•
Avira Desktop: Important System Update - requires immediate
action
• Baidu Antivirus: Important System Update -
requires immediate action
• Cloud Antivirus Firewall:
Important System Update - requires immediate action
•
ESET NOD32 Antivirus: Important System Update - requires
immediate action
• Kaspersky Anti-Virus: Important
System Update - requires immediate action
• McAfee
Personal Firewall: Important System Update - requires
immediate action
• Norton AntiVirus: Important System
Update - requires immediate action
• Norton Internet
Security: Important System Update - requires immediate
action
• Norton 360: Important System Update -
requires immediate action
• Symantec Endpoint
Protection: Important System Update - requires immediate
action
• Trend Micro Titanium Internet Security:
Important System Update - requires immediate
action
Although the subject line changes, the attached zip file containing the malicious executable stays the same. Once the malware is executed, a connection is made to networksecurityx.hopto.org to download another file. The malware uses a process called ozybe.exe to perform tasks.
Symantec recommends
The Skeptic
scanner of Symantec
Email Security.cloud can block this and similar emails
before it can even reach the end user. In addition, Symantec
also detects the files associated with this attack using the
following signature names:
• Trojan.Gen
• Trojan.Zbot
• WS.Viral.1
Symantec advises following best practices to avoid
becoming a victim of social engineering spam attacks:
•
Do not click on suspicious links in email messages.
•
Do not open any attachments from recipients you do not know
or expect an attachment from.
• Do not provide any
personal information when replying to an email.
• Use
comprehensive security software, such as Norton Internet Security or
Norton 360, which protects you from phishing and social
networking scams.
• Exercise caution when clicking on
enticing links sent through email or posted on social
networks.
Read the full Symantec Security Response
blog:
http://www.symantec.com/connect/blogs/fake-av-software-updates-are-distributing-malware
Click for big version.
ENDS


 Gordon Campbell: On The Hikoi Aftermath
Gordon Campbell: On The Hikoi Aftermath Free Speech Union: Fair Digital News Bargaining Bill Likely To Restrict Access To Information, Polling Shows Most Oppose
Free Speech Union: Fair Digital News Bargaining Bill Likely To Restrict Access To Information, Polling Shows Most Oppose Auckland Transport: Driver Safety Screens Now Rolling Out Across Auckland’s Bus Fleet
Auckland Transport: Driver Safety Screens Now Rolling Out Across Auckland’s Bus Fleet People Against Prisons Aotearoa: 'Expect Resistance' - Community Group Pushes Back Against More Cops With Guns
People Against Prisons Aotearoa: 'Expect Resistance' - Community Group Pushes Back Against More Cops With Guns Greenpeace: New Zealand Drops In Global Ranking On Climate Action
Greenpeace: New Zealand Drops In Global Ranking On Climate Action PSA: Spending Cuts Need To Stop - PSA Urges Govt To Listen To Economists
PSA: Spending Cuts Need To Stop - PSA Urges Govt To Listen To Economists Stats NZ: National Population Estimates: At 30 September 2024 (2018-base)
Stats NZ: National Population Estimates: At 30 September 2024 (2018-base)


